The process of sending an email involves several technical components and protocols. When you send an email, it is first composed in an email client, such as Gmail or Outlook, which is a program that allows you to access your email account[2][4]. The email client communicates with an outgoing email server, which is responsible for sending the message out to the recipient’s email server[2][4]. The outgoing email server uses Simple Mail Transfer Protocol (SMTP), which is a protocol used for sending email messages over the internet[2][4]. The server must ensure that the email is properly formatted, including the sender and recipient addresses, subject line, and body content[2][4]. Once the email is sent, it is routed to the recipient’s incoming email server, which is responsible for receiving the email and storing it in the recipient’s mailbox until they access it[2][4]. The incoming email server can be configured with various settings to help filter out spam messages and prevent unauthorized access to the recipient’s mailbox[2].
The recipient’s email client retrieves the message using standards like the Post Office Protocol (POP) or Internet Message Access Protocol (IMAP)[2][4]. POP downloads a copy of the email to the client’s device, while IMAP keeps the email stored on the server and allows the client to access it remotely[2][4].
In addition to SMTP, POP, and IMAP, there are several other email protocols that are used to govern email transmission and delivery. These include DKIM (DomainKeys Identified Mail), which is used to verify the authenticity of email messages and ensure that they haven’t been tampered with, and SPF (Sender Policy Framework), which is used to verify that an email message was sent from an authorized source[2]. DMARC (Domain-based Message Authentication, Reporting and Conformance) is used to prevent email spoofing and provide visibility into email delivery[2].
Email authentication is the process of verifying the authenticity of an email message and ensuring that it wasn’t sent by a spammer or other malicious actor[2]. This is accomplished using various email authentication protocols, such as DKIM, SPF, and DMARC[2]. Email deliverability refers to the ability of an email message to be delivered to its intended recipient[2]. There are many factors that can impact email deliverability, including the sender’s reputation, the content of the email message, and the recipient’s email provider[2]. To improve email deliverability, it’s important to properly authenticate your email messages and maintain a good sender reputation[2].
In the case of spamming a large number of companies or HR departments with your CV, it is not recommended and can be considered as spamming. This can damage your reputation and can lead to your email being blocked by the recipient’s email server. It is always recommended to send your CV to specific companies or HR departments that you are interested in and have a legitimate reason to contact. This will increase the chances of your email being read and responded to, and will also help to maintain a good sender reputation.
Citations:
[1] https://bird.com/guides/email-message-flow-sending-delivery
[2] https://www.mailpro.com/blog/email-infrastructure
[3] https://chainlinkmarketing.com/how-email-works-blog/
[4] https://www.mail.com/blog/posts/what-happens-when-an-email-is-sent/56/
[5] https://www.namecheap.com/support/knowledgebase/article.aspx/10589/2179/how-does-email-work/
In fact, you have been designated as a spammer (your IP in fact) because you have, for example, made mass mailings with your Yahoo, Gmail or Hotmail mailbox using ICC (Invisible Carbon Copy) or BCC (Blind Carbon Copy). In conclusion, If your primary email is a web-based email (Yahoo, Gmail, Hotmail….). You will be blacklisted and lose your IP address the moment you start sending your first group of illegal mass emails. use a specific email for work research not your personal. The worst thing that you may not know is that a web-based email provider follows you like a sheepdog follows these sheep and as soon as it detects abnormal activity, it blacklists you in its own system.
worse, you are using bulk email sending software and you think that you have created an “safe environment”.
It’s theorical and you have the right to think that your IP will be protected using the following tools like:
A Proxy-server which is a proxy-home server: It’s is a computer that intercepts and manages traffic between two devices, networks or protocols. A proxy is a gateway that acts as an intermediary between your computer and the websites and Internet services you use for send your CVS’s . In fact, if the blacklisting software detects 3 times Your IP in less of 3 seconds, you pass in Blacklist!
A VPN or virtual private network which creates a private network connection between devices over the internet. VPNs are used to transmit data securely and anonymously over public networks or security software. All the IP used in VPN have been used millions of times and they are blocked; a VPN is secure for a surfing or for a specific service you use (your bank by example) but never for do mass email sending. It’s a non-sense because the antispam organization have the tools for identify the real IP which will pass in Black list.
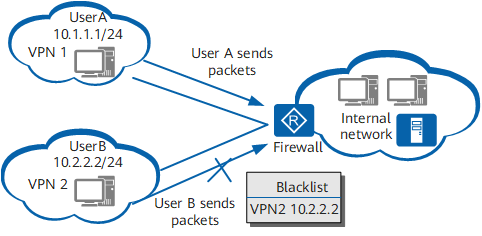
- Can A VPN Get Around An IP Banned/Blacklisted?
A Virtual Private Network or VPN is a smart piece of software that routes your traffic through secure, encrypted servers and also changes your IP address but a lot of people have used before you the IP. For this reason, they cannot be used to get around IP bans or blacklists, when your current IP address gets banned from using a particular platform or service for whatever reason. they are also banished and black listed. As with many things in technology, there isn’t a clear-cut black and white answer, but here is a general summary answer:
- A VPN can sometimes allow a user to get around an IP ban because they mask your real IP address and location and replace it with a new one that is hopefully not banned but be confident that all the IP from a VPN software are banned from the moment they appear.
- However, many VPN IP addresses are also blacklisted, so it may require some persistence, along with the creation of new accounts on many platforms, with new usernames and email addresses not used previously.
- In other words, while it can work using a VPN to get around IP bans and blacklists, it can be a hit and miss process. You might have to try a few different VPNs to get it to work, plus setting up whole new accounts if certain platforms ban entire accounts for infringements and not just IP addresses. Again change of ISP is the best alternative
https://weakwifisolutions.com/can-a-vpn-get-around-an-ip-ban-blacklist
Can VPN bypass IP ban?
Adjust your IP address through VPN or Proxies-home software. Another good solution for bypassing an IP ban is simply getting a fresh IP address. One way of doing this is by using a trustworthy proxy-home service generation 3, which can change your IP address and your apparent internet service provider (ISP) every seconds, This type of service exist but it’s very expensive and reserved to big companies
Does a VPN conceal your IP?
With a VPN, your online activities are anonymized and protected because the VPN masks your IP address and encrypts your data throughout the entire transmission. But if you are using a standard commercial VPN take care, mainly their IP are banned since a long time!
https://uk.norton.com/blog/privacy/how-a-vpn-can-help-hide-your-search-history
- Ghost IP address software able to create a ghost IP instead of your own IP. In fact, it’s very complicate to use an efficient Ghost IP address software because the software must be adjusted to your computer model with specific components, your Operator system (Windows or Apple) and the mass mailing software’s you use}
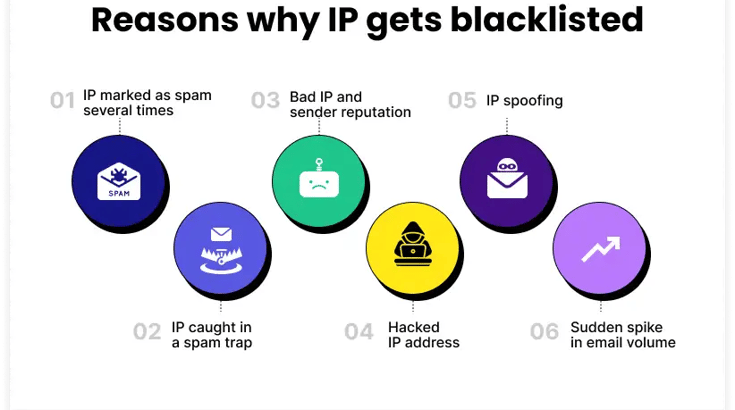
The 11 worst reasons why your emails are blocked and you pass in Black lists by Gmail, Yahoo, Hotmail to other web-based ISPs
Did you know that your IP addresses for sending email could be blocked? This blocking can cause email with your CV and emails in general not to reach their destination or to arrive with a long delay. The good news is that this can be prevented. Keep reading. Before telling you how to prevent this, we list here the reasons why these blockages can occur:
The 11 worst reasons why your emails are not arriving:
- High-rate Spam reports in batches of 1000 emails: A high rate of reports of Spam occurs if out of a sample of 1000 emails sent, at least 0.03% of have marked your email as spam (by pressing the Spam button in Hotmail, Gmail, Yahoo, etc). We talk about how to prevent this below.
- Excess of bounced emails: If on a sample 1000 emails at least 5 % bounces, it can be inferred that emails are being sent to mailboxes built with random names, purchased, rented or obsolete lists.
- Sending emails to Spam traps is the worst you could do. Spam trap is an anti-spam technique used by the Internet Service Providers, based on the constant creation of email addresses in a secret way, which are classified as “traps”. After their creation, these addresses are not shared or published anywhere, for this reason they would have no reason to receive any communication. Consequently, if you ever have a campaign that reaches one of these addresses, the whole campaign of CV to recruiter will be considered as SPAM and your IP addresses will be blocked.
- Sending emails with links pointing to domain names that are on black lists.
- Sending emails that are later reported as Phishing campaigns in Gmail and other web based ISPs.
- Sending emails with Virus or Malware attachments.
- Mailings from senders’ domain names that are blacklisted.
- Mailings from mailboxes that do not exist.
- Sending emails from senders that do not have the Sender Policy Framework(SPF) configured authorizing the IP addresses from which the emails are sent.
- Sending email with content that do not match with the company you will contact could block your entire IP for other emailing CV campaigns. For example: movie or big photos,
- Banishment of your geographical area.